Hey there, fellow tech enthusiasts! After spending over a decade wrestling with cloud infrastructure, I’ve learned that managing multiple AWS accounts is like juggling flaming torches – exciting but potentially dangerous if you don’t know what you’re doing. Today, let’s dive into AWS cross account access, a game-changing feature that’s saved my bacon more times than I can count.

Why Should You Care? 🤔
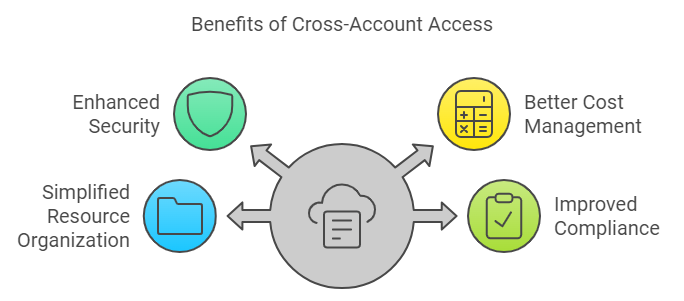
In the modern cloud landscape, using multiple AWS accounts isn’t just a luxury – it’s a necessity. Whether you’re managing development, staging, and production environments, or handling different business units, proper cross-account access is crucial for:
- 🛡️ Enhanced security through isolation
- 💰 Better cost management and billing
- 🎯 Simplified resource organization
- 🔍 Improved compliance and auditing
The Basics: How AWS Cross Account Access Works 🔧
Think of AWS cross-account access like a secure VIP pass system. Just as you wouldn’t give everyone keys to every room in a building, you can control who gets access to what across your AWS accounts. The main components are:
- IAM Roles – These are like special security badges
- Trust Relationships – The rules about who can use these badges
- Policies – What the badge holders can actually do
Real-World Example: Development Team Access 💻
Let’s say you’re managing a startup with three AWS accounts:
- Production (Account ID: 111111111111)
- Staging (Account ID: 222222222222)
- Development (Account ID: 333333333333)Here’s how to set up cross-account access for your development team:
- First, create an IAM role in the staging account:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::333333333333:root"
},
"Action": "sts:AssumeRole"
}
]
}- Attach the appropriate permissions policy (e.g.,
AWSLambdaReadOnlyAccess) - In the development account, grant developers permission to assume the role:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::222222222222:role/StagingAccess"
}
]
}Best Practices for AWS Cross Account Access 🌟
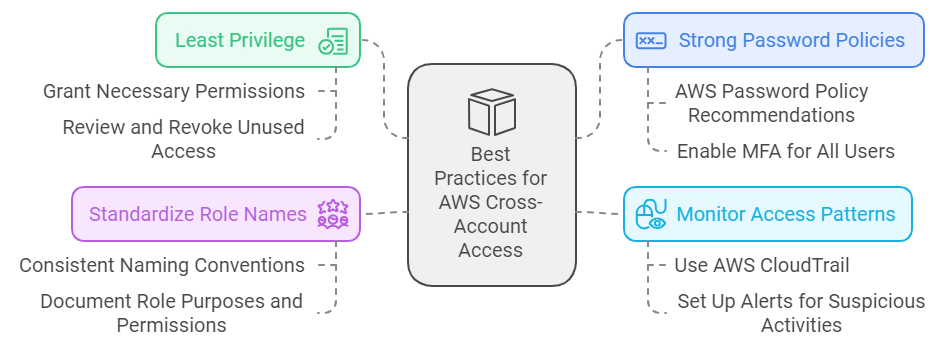
- Use the Principle of Least Privilege
- Only grant necessary permissions
- Regularly review and revoke unused access
- Implement Strong Password Policies
- Check out AWS’s password policy recommendations
- Enable MFA for all users
- Monitor Access Patterns
- Use AWS CloudTrail for audit logging
- Set up alerts for suspicious activities
- Standardize Role Names
- Use consistent naming conventions
- Document role purposes and permissions
Tools That Make Life Easier 🛠️
- AWS Organizations
- Centrally manage multiple accounts
- Apply service control policies
- AWS SSO
- Single sign-on for all accounts
- Integrate with existing identity providers
- AWS CLI with Profiles
aws configure --profile staging
aws s3 ls --profile stagingTroubleshooting Common Issues 🔍
- Access Denied Errors
- Check IAM role trust relationships
- Verify policy permissions
- Ensure correct account IDs
- Session Expiration
- Default session duration: 1 hour
- Can be increased up to 12 hours

FAQ Section
What is the maximum number of AWS accounts I can have? 🤔
AWS Organizations allows you to create and manage up to 10,000 accounts, but you’ll need to request limit increases for large-scale deployments.
Can I use cross-account access with AWS Lambda? 📦
Yes! You can configure Lambda functions to assume roles in other accounts. Check out the AWS Lambda cross-account tutorial.
How secure is cross-account access? 🔒
When properly configured, it’s very secure. AWS uses industry-standard encryption and authentication methods. The key is following security best practices and regularly auditing access.
What’s the difference between resource-based policies and IAM roles? 📝
Resource-based policies attach directly to resources (like S3 buckets), while IAM roles are entities that users or services can assume to obtain temporary credentials.
Wrapping Up 🎁
Cross-account access in AWS is like having a well-organized set of keys for a large building – when done right, it provides security, flexibility, and peace of mind. Remember to start small, test thoroughly, and gradually expand access as needed.
Want to learn more? Check out these resources:
Happy cloud computing! Feel free to drop your questions in the comments below, and don’t forget to share this guide if you found it helpful! 🚀
P.S. Keep an eye on your AWS bill – proper cross-account access can help prevent unexpected charges, but it’s always good to set up cost alerts just in case! 💰
Next: Unlock the Power of AWS Lambda Concurrency for Effortless, Scalable Success🚀



![AWS CodePipeline: The Ultimate Guide to 10X Your Deployment Speed [2024] aws codepipeline](https://devnotes.tech/wp-content/uploads/2024/11/aws-codepipeline-150x150.jpg)